This is a rellay fun box aimed to teach port knocking. We portknock the box at three instance to get to the ssh port but, the shells aren’t stable TTY shells and we have to find our way in. Finally we exploit the OverlayFS exploit(CVE: 2015-1328) to gain root.
Initial Foothold
Host Discovery
Initially we are dropped into a network containing the vulnerable host and we scan for our target on the
Network: 192.168.43.0/24
Confirming our results with Nmap
Host Scanning
Next we start off by scanning the host for open ports we find an http server running on port 80
On opening this website in browser, we discover a link to download a Pcap file.
Port Knocking
Opening this pcap file in wireshark, we discover the Port Knocking Sequence of 7000 8000 and 9000. This Knocks open 8888
Connecting to this port using netcat, we are told of a hidden directory
Visiting this path on the website gives us a link to download another Pcap file.
Opening this Pcap with wireshark, we found another hidden message in tcp stream
Google translator helps us to decode this secret message
This message tells us to knock Port in sequence 1 3 3 7 This helps us in Knocking opens port 1337 . Connecting to port 1337 using netcat reveals another hidden directory.
Visiting this directory on browser, it containing username of Beavis and ssh port opening sequence encrypted which I thought of initally as password.
Decoding this messsage, we get the final port knocking sequence to open up ssh port 22 whein knocked in the order 8888 9999 7777 6666
SSH port opened
SSH onto the Machine
While we try to ssh as the user Beavis we found the actual ssh credentials
| |
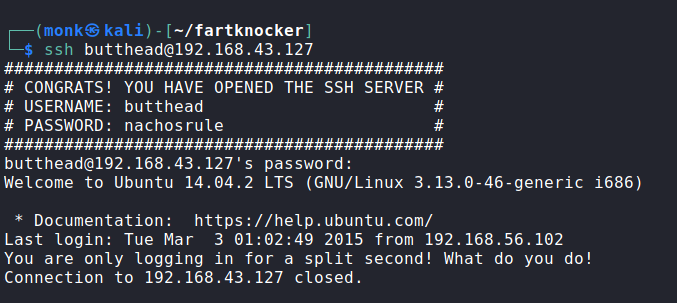
But our shell is immediately exited when we login successfully. To solve this, we run the /bin/bash command followed by the ssh command. This gives us a shell on the box.
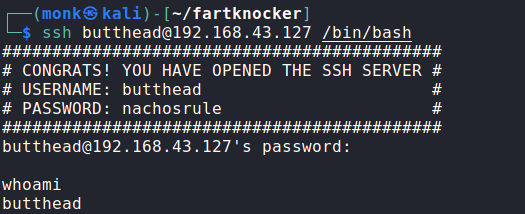
Escalation
Further Enumerating the box looking for any low hagning fruit or misxonfiguration doesnot help so, we try to look for kernel exploits. But, lets ennumerate the Host first.
Using Searchsploit to find desired exploit
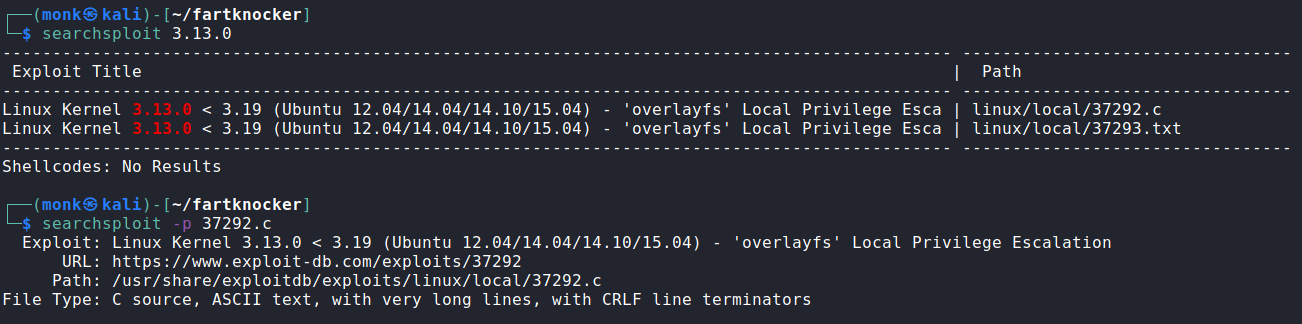
We transfer the exploit 37292.c to our target using Python
| |
Compile the exploit on the target and exploit the system
| |