This is a short writeup for all the challenges of the VIITCTF V3 organized by the ACM Student Chapter of VIGNAN’s Institue of Information Technology.

Introduction
This was a beginners level CTF and the challenges were mostly from OSINT, Crypto, Stego, Reverse.
Here is an Image of my challenges dashboard. I was eventually able to upsolve all the challenges.
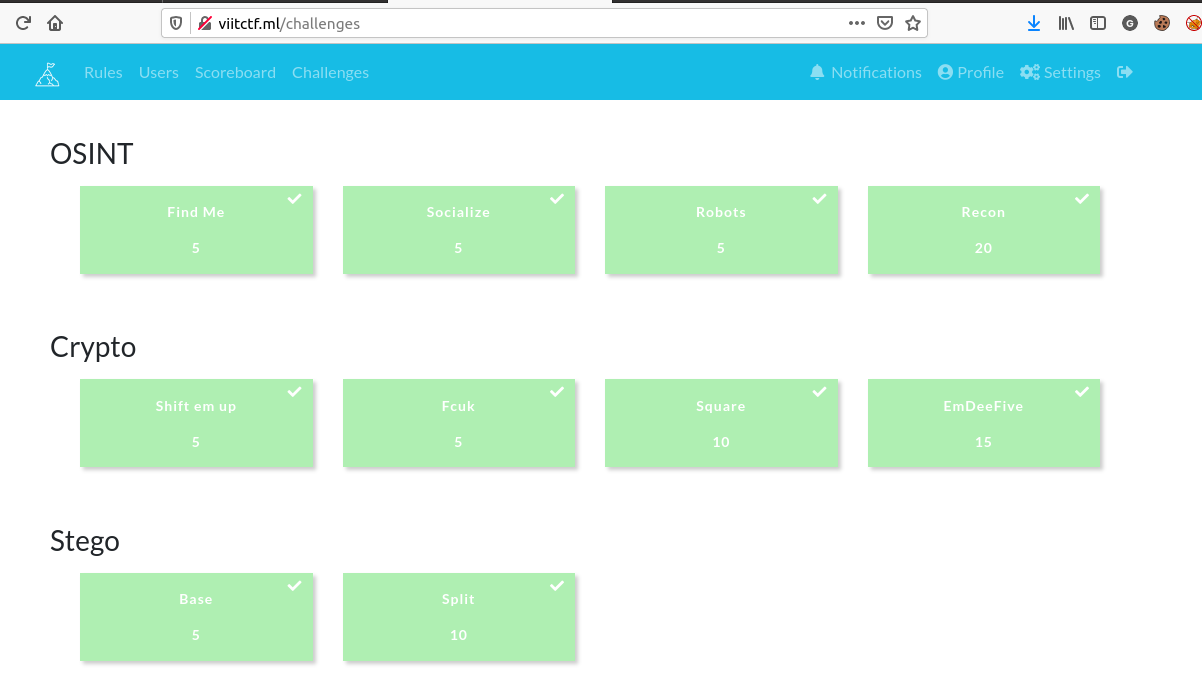
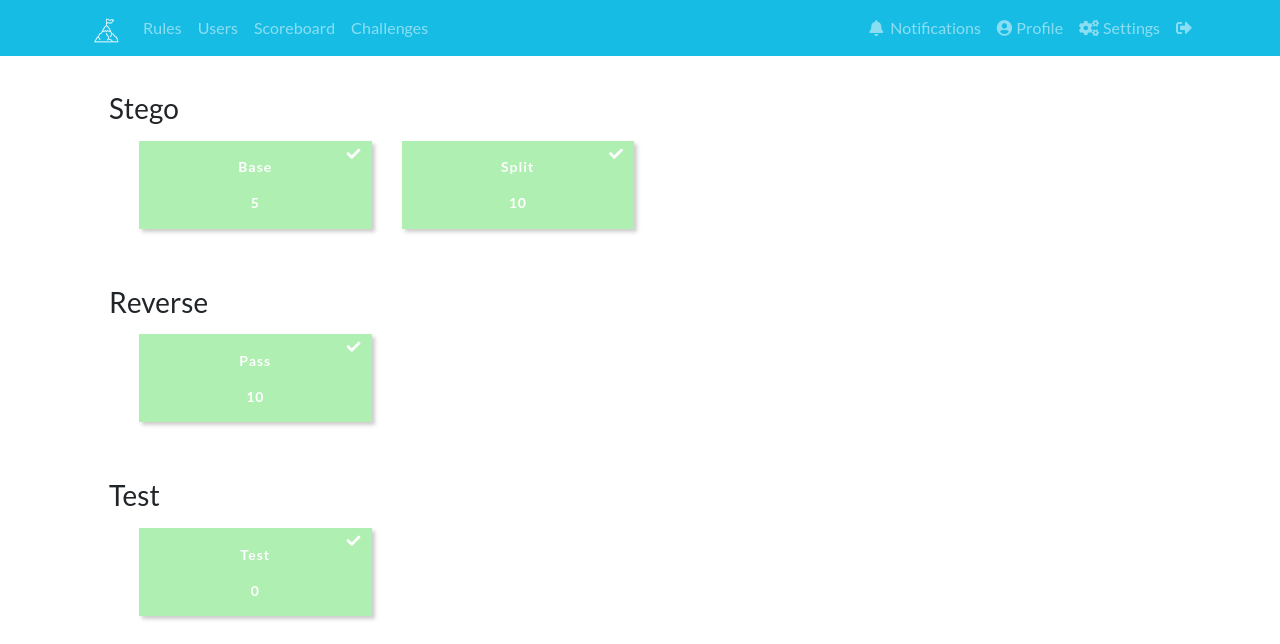
Lets take a look at all the challenges.
Test
Test : 0 Points
This was a dummy challenge to keep a track of the total number of participants and also introduce them to the flag format VIITCTF{.*} Here we simply had to copy paste the flag to solve it.
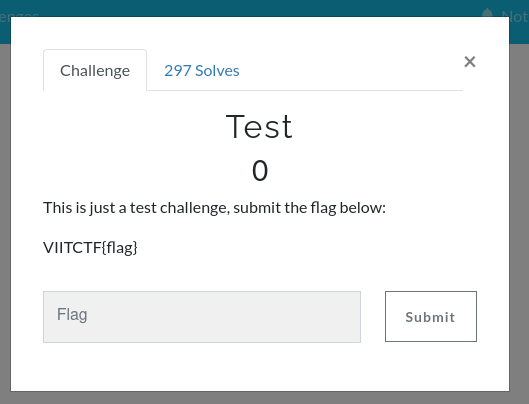
Answer: VIITCTF{flag}
OSINT
This section had four challenges which is going to test our skills of source code inspection, Passive recon to gather user information, guessing common directories and looking through DNS records.
Find Me : 5 Points
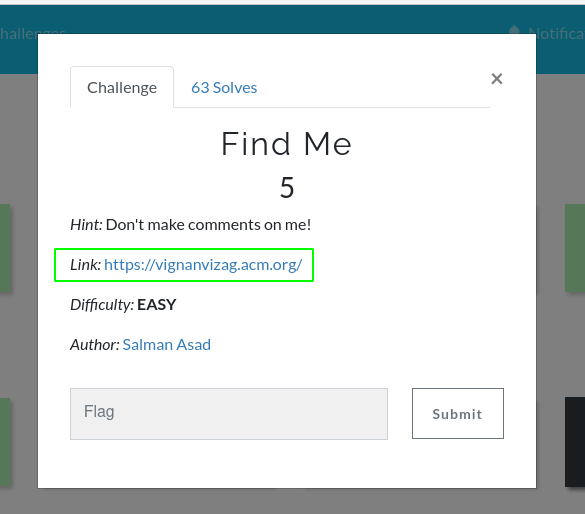
In this challenge we are provided with the following url. Now, as the first hint of the challenge suggested don’t make comments on me. This generally refers to the bad practices where developers tend to leave their credentials or some private data in source code comments. So, I started with looking into the source code for any suspicious comments.
Socialize : 5 Points
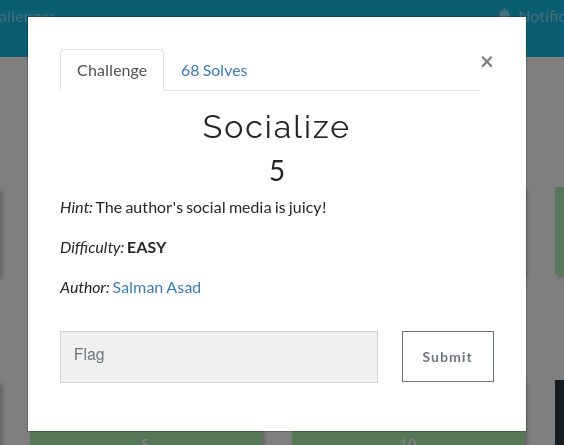
In this question we are given no exact information but, the twitter handle of the user and the promt tells us that the users social media contains some juicy info which points out that there might be flag hidden somewhere on his social media accounts.
We begin by looking into his twitter account @deathflash1411 . Here we find a link to his website.
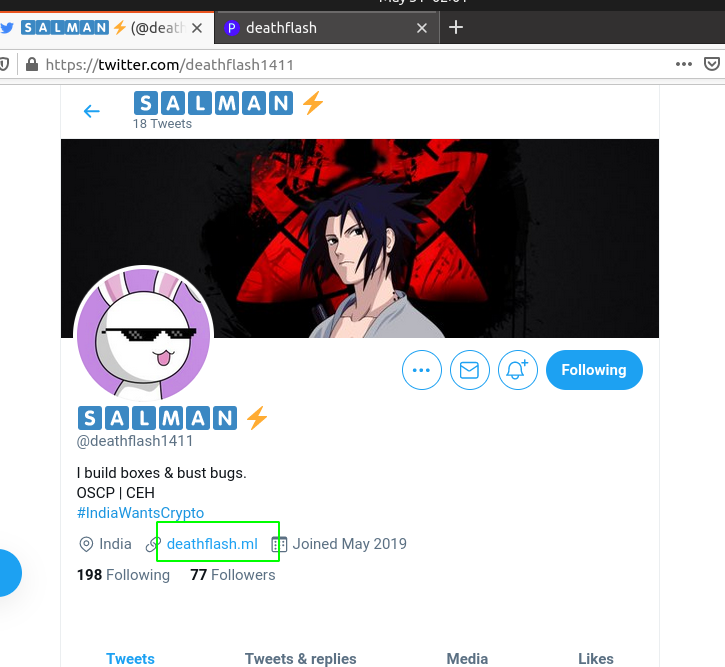
On visiting his website we can see all of his social links on the footer.
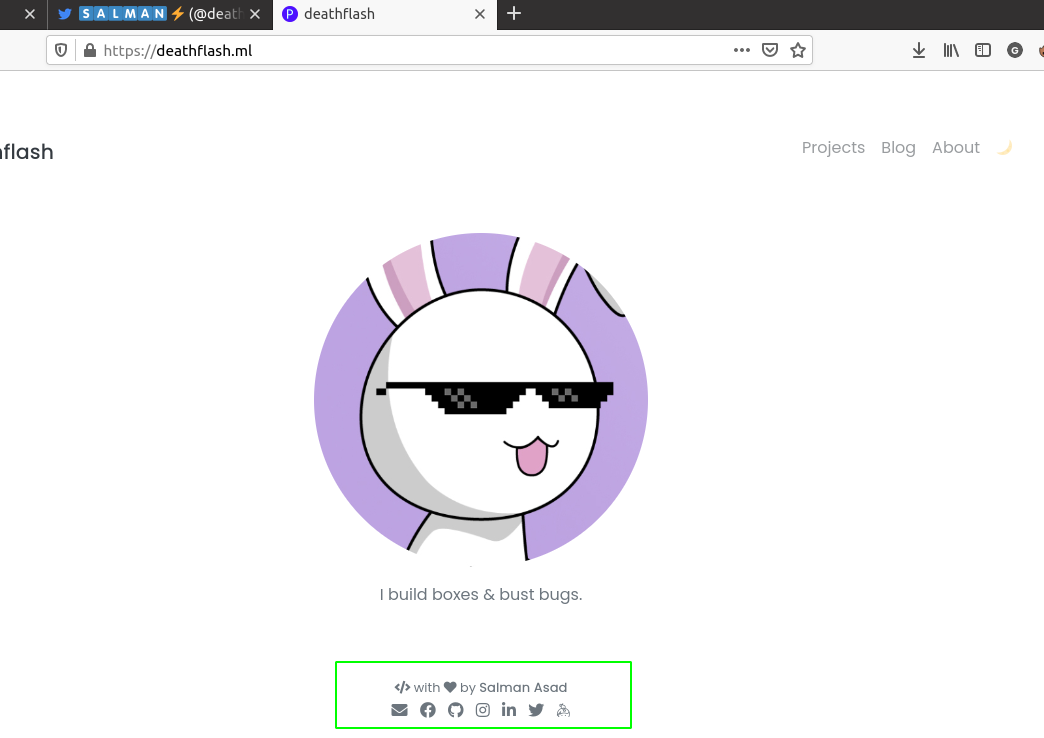
I looked for all the available possibilities and finally found something useful on his instagram profile.
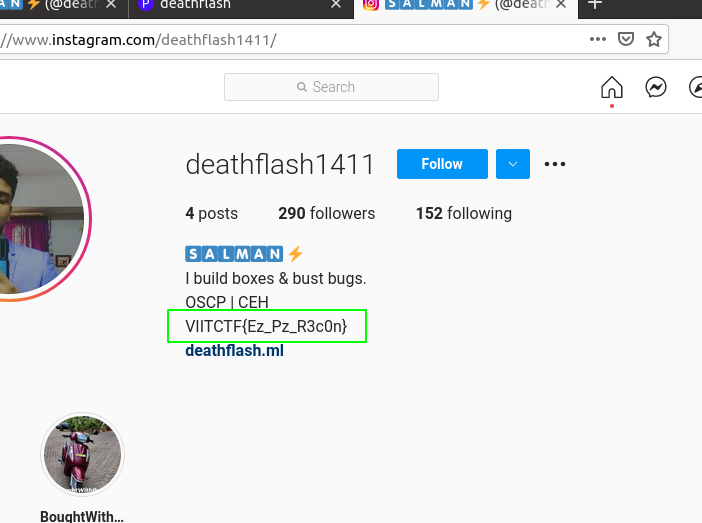
Answer : VIITCTF{Ez_Pz_R3c0n}
Robots : 5 Points
In this challenge we are given a link to the defmax.io website. As the challenge prompt and the question names had robots in it I clearly planned to look for the robots.txt file as this is one of the most common files used by web crawlers. It has the permissions for the web crawlers weather they should index a particular page on search results or not based on their user agents.
Fortunately upon visiting defmax.io/robots.txt I found the flag.
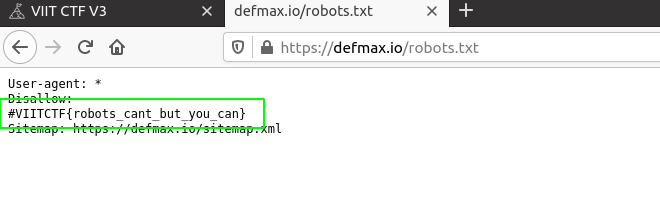
Answer: VIITCTF{robots_cant_but_you_can}
Recon : 20 Points
In this challenge we are provided with the link to defmax.io website and we are to find the IP address behind cloudflare.
Now, at a first glance you may want to try to find out the IP by looking for the A records of the DNS or use some other tools to get an insight of all the records of the Domain like AAAA ,MX, NS, CNAME, TXT etc. but, I we can find no information here. Even the A records has got the IPv4 address.
A short snap of the information retrived by using dig(Domain Information Gathering) tool is shown below.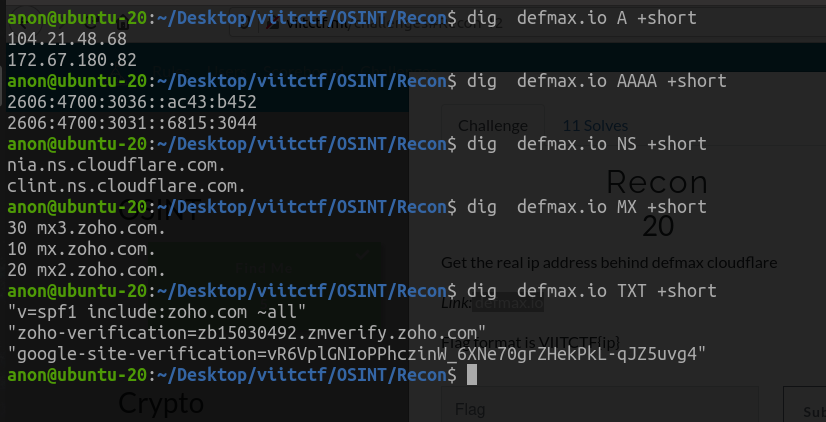
As stated the IP clearly belongs to Cloudflare and its of no use. So, next I came across this amazing tool Censys.io. This tool help us in gathering information of host. It is a great tool to get an overview of the host just using the domain name.
So, searching for defmax.io on censys I found three IP addresses and the one which appears at the bottom is in fact the correct IP address. Which can be verified by manually visiting the Urls.
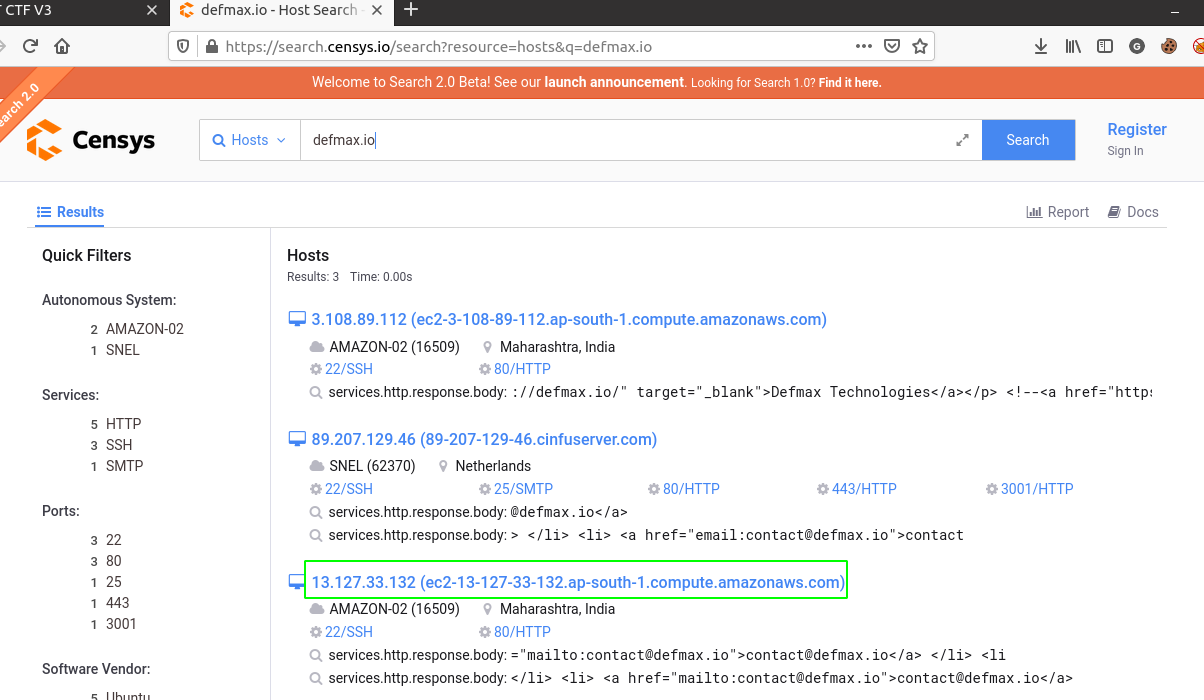
Answer: VIITCTF{13.127.33.132}
CRYPTO
Shift em up : 5 Points
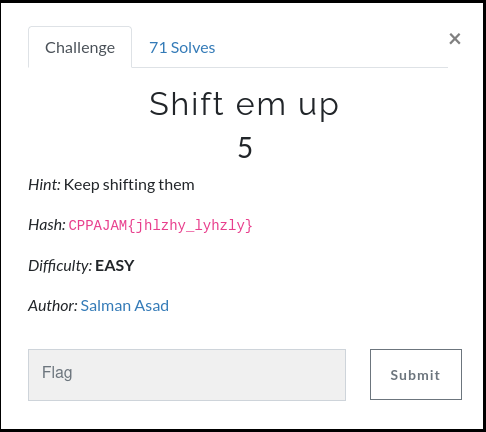
In this challenge we are provided with the following cipher CPPAJAM{jhlzhy_lyhzly} and the hint also tells us to keep shifting. This indicates that it might be related to caesar shift cipher. So, I pasted the cipher in Cyberchef and using the Rot13 decoder I kept incrementing untill I found the flag on shift 19.
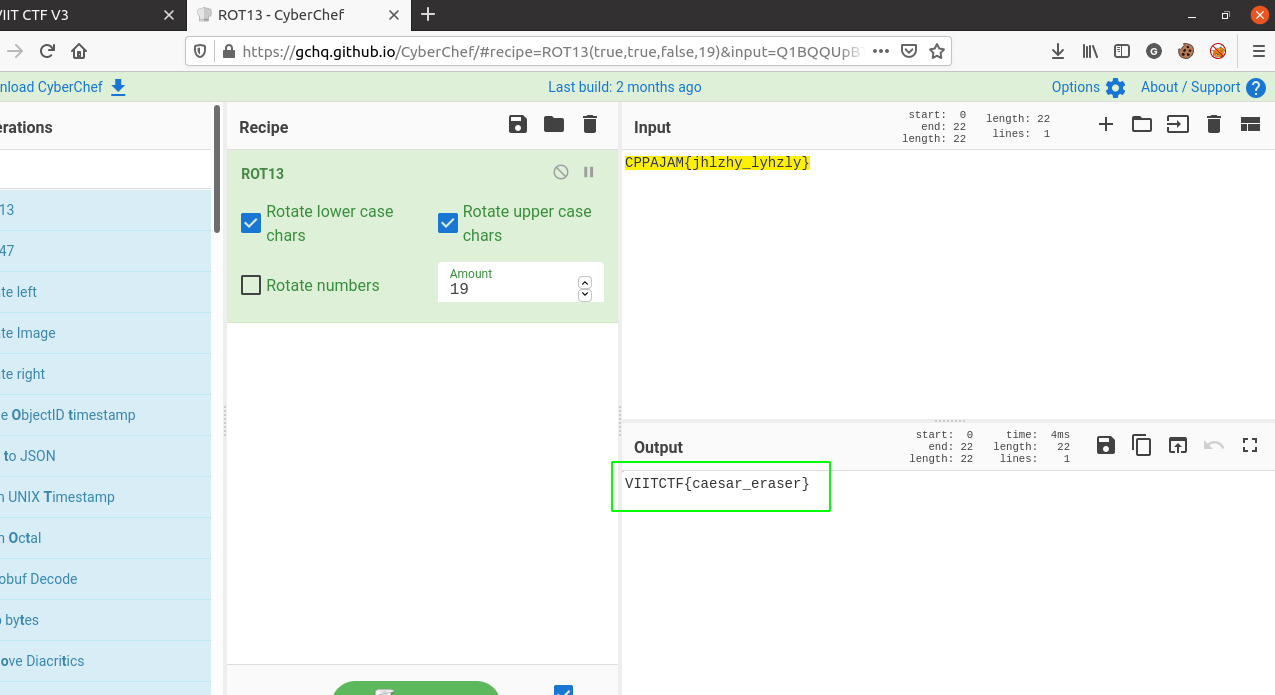
Answer: VIITCTF{caesar_eraser}
Fcuk : 5 Points
In this challenge as the name of the file and the challenge indicates, jsf.txt this is associated with the JSfuck esoteric programming language. It can also be guessed by the IIFE expression at the end of the message.
So, we use thid JSFuck decoder from dcode.fr
Pasting the cipher here and decoding gives us the flag.
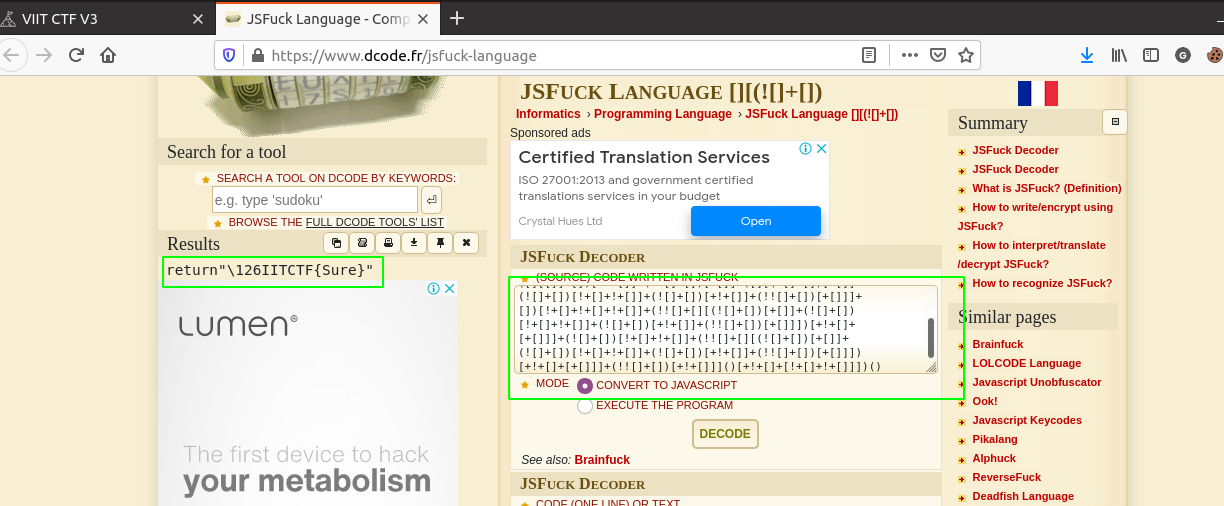
Answer: VIITCTF{Sure}
Square : 10 Points
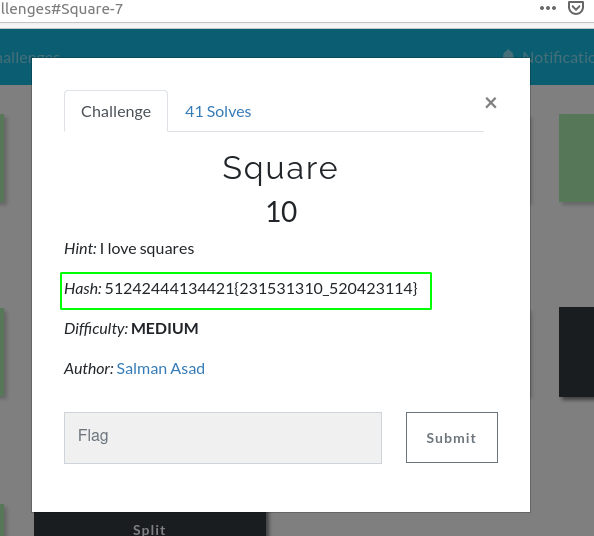
This challenge involves the Polybius Square Cipher. To decode this we use this Polybius Square Cipher Dcoder-Cryptii
Simply pasting the hash and allowing for foreign characters and decoding gives us the flag.
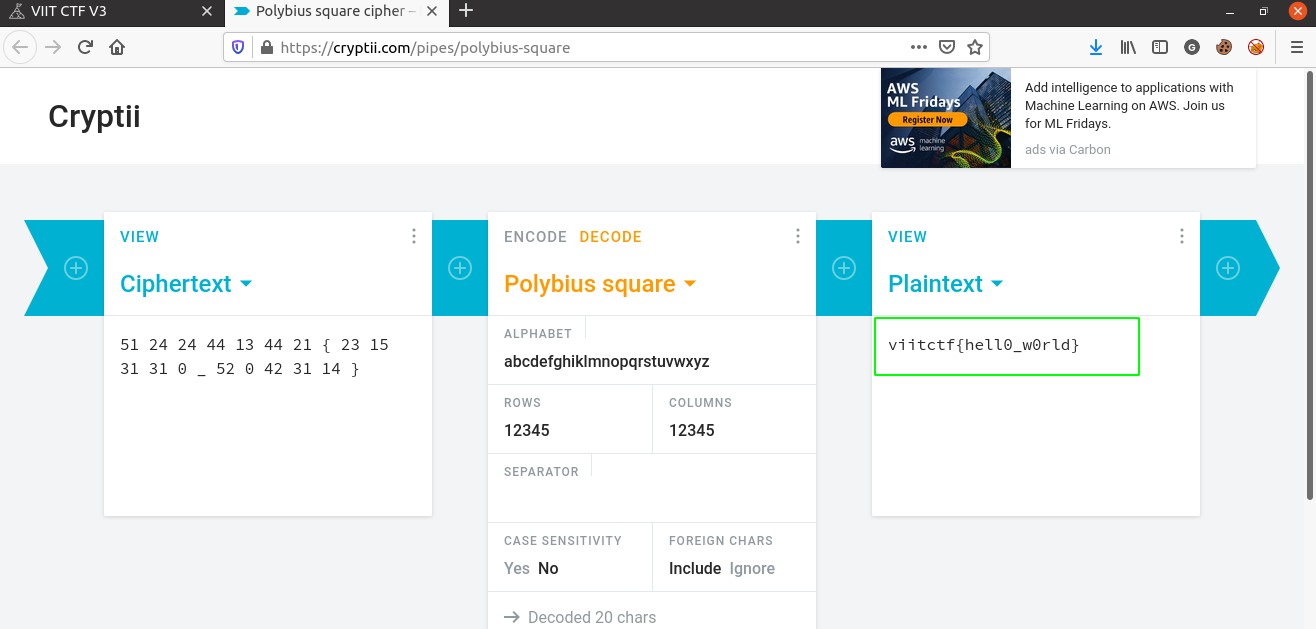
Answer: VIITCTF{hell0_w0rld}
EmDeeFive : 15 Points
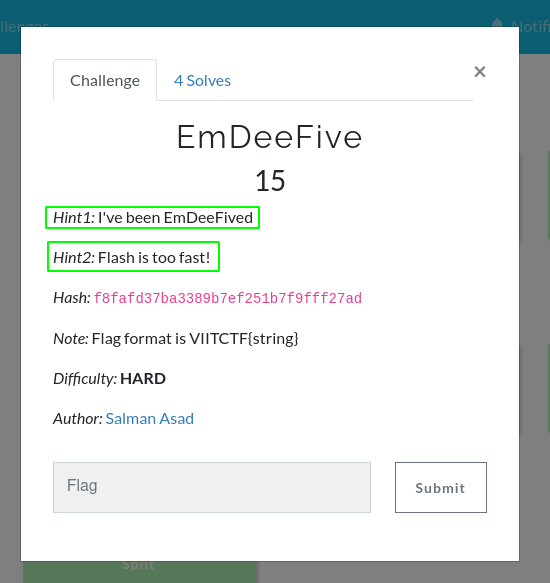
This was a relatively difficult challenge which I was able to solve after the CTF got over.So, in this problem there are two things to note. First our wordlist must have flash in it. And Second, this is not a simple MD5 encoding which we can crack using John or Hashcat as the string has been MD5 hashed 5 times as 1st hint tells us.
So, I came across this amazing blog which describes this and also it has a mirror to original MDxfind as the original source seems missing.
First we start off by generating the wordlist. I will be generating this using the rockyou.txt wordlist.
| |
We will use this wordlist for the hash cracking.
| |
Here -h specifies the hashtype ,-i specifies the iterations and -f specifies the hashes file followed by the wordlist file
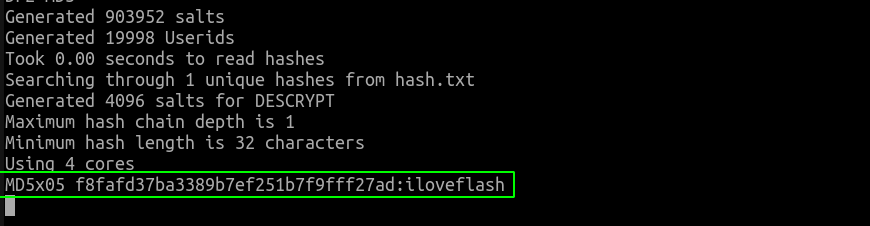
Answer: VIITCTF{iloveflash}
Stego
Base : 5 Points
In this question we are provided with some base32 encoded data as we can see below it has characters in the range of A-Z and 2-7.
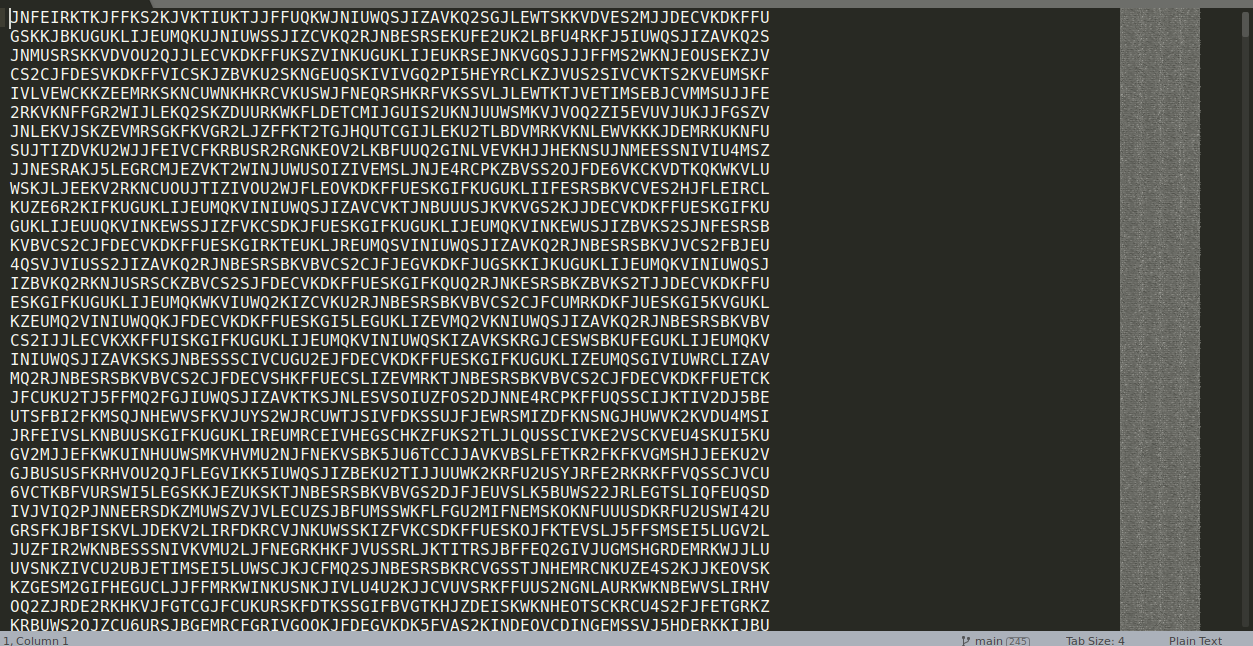
So, we see try to decode it online on cyberchef using decode from base32 and the output is again base32 encoded so, decoding from base32 three times we finally get some RAW data which after some close inspection looks like a PNG image data due to PNG , IHDR and IEND strings in them.
Also an alternate way of this this can be using a base32 decoder offline.
| |
So, I downloaded the raw data and saved as PNG. This png gives us the flag.
Node: While downloading the data save it as filename.png
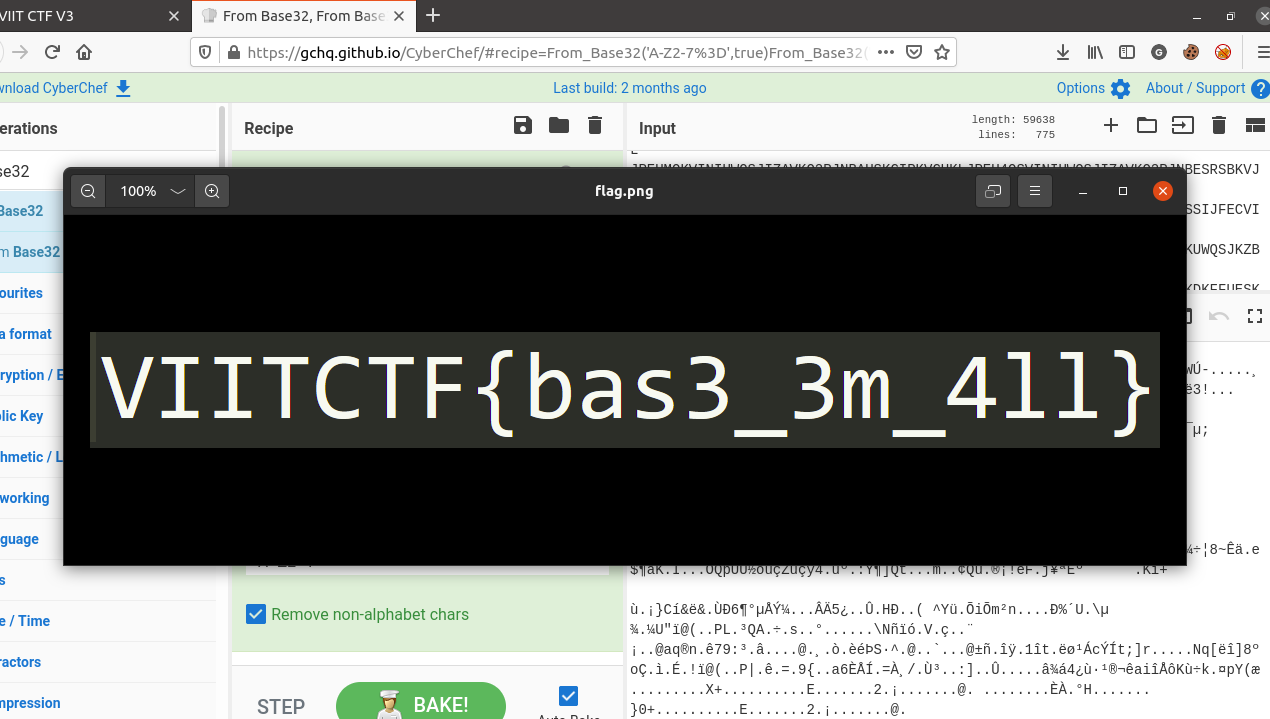
Answer: VIITCTF{bas3_3m_4ll}
Split : 10 Points
In this challenge we are given with chunks of QR code inside a zip file and we can simply use photoshop to allign the qr code using trial and error and finally we get this QR code.

Next we can use a tool called zbarimg to read the contents of the qr from the terminal itself.
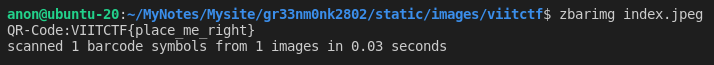
Answer: VIITCTF{place_me_right}
Reverse
Pass : 10 Points
In this challenge we are provided with a binary and we need to reverse it.
Now There can be multiple ways of doing it and we can use various tools to reverse it, but the easiest of all is to reverse the source code using Ghidra or Radare2.
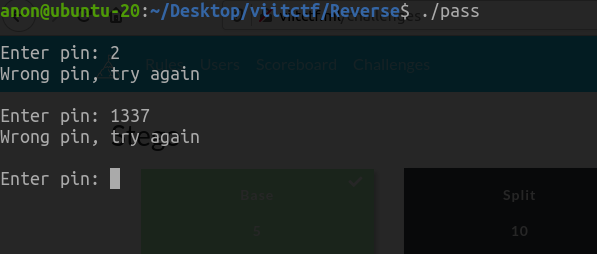
So, in this challenge we are to find the PIN of this binary. We start as usual with analysis and by using strings command to get all the printable ascii characters but, its of no use.
So, next we open the binary in Ghidra and instantly we get the PIN 0x583 or 1411 in numeric.
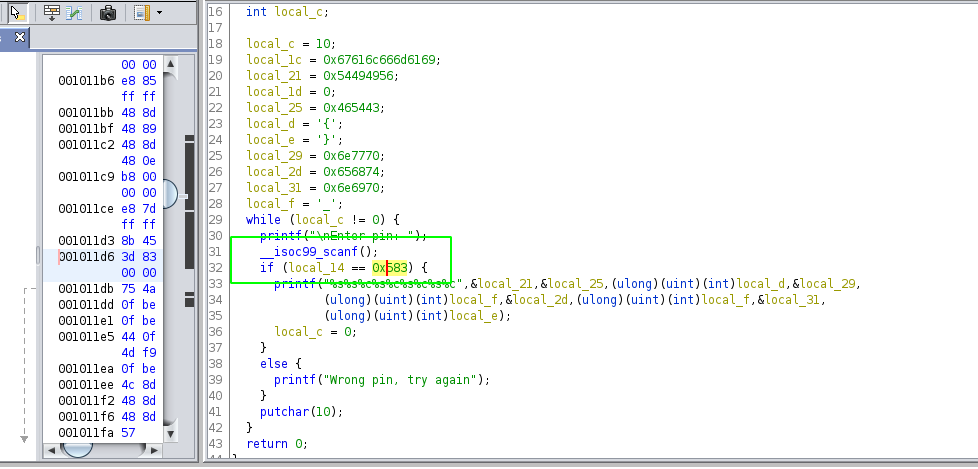
Also doing the same in Radare, analyzing the function, seeking to the main function and printing it gives the flag.
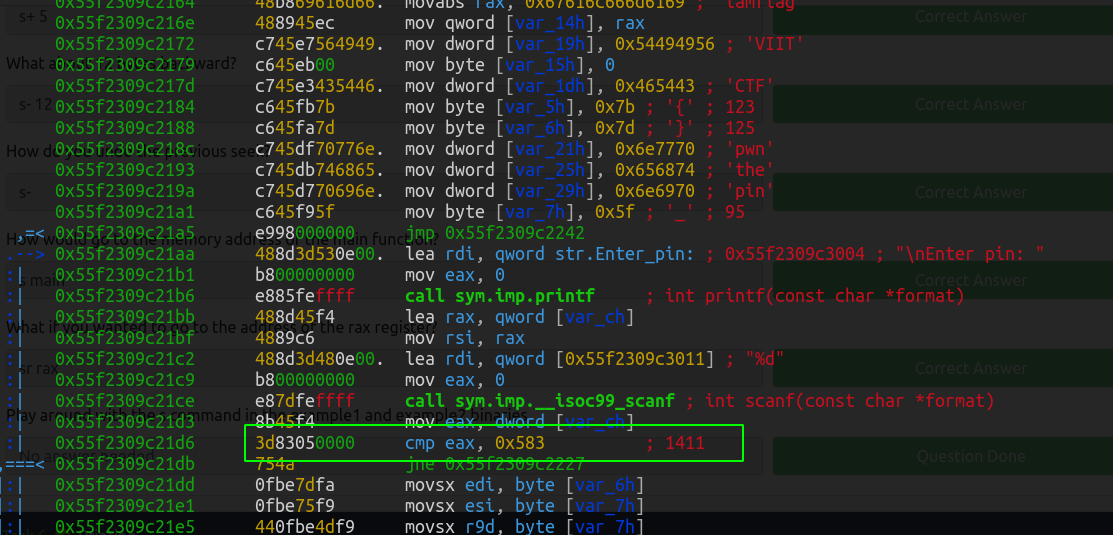
Hence using the PIN as 1411 we, get our flag.
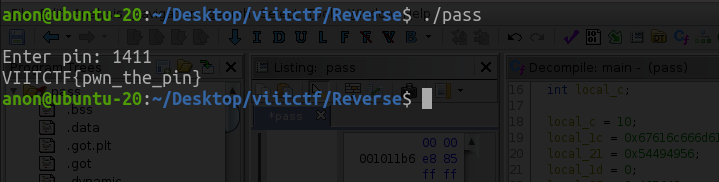
Answer : VIITCTF{pwn_the_pin}